As the epidemic heats up, we must work from home to keep everybody safe. It has absolutely changed our way of working, along with these changes, email being a primary way to communicate, including transfer files to other colleagues and customers. But in recent years, the risk of email being attacked has also increased.
Everyone must have heard of mail fraud (or email scams), and hackers keep changing to new methods to steal your information through email. Their target is not only general people but also corporate. A large number of emails were attacked, causing financial loss and decreasing business credibility.
Table of Contents
Common email scams
Phishing
This scamming method attempts to steal personal information such as login passwords, bank accounts,etc through emails that contain virus links or malicious programs.
Hackers pretend to be a reputable company, such as bank, credit card company, social media or government agency to send a large number of emails by using email accounts that look like public accounts from government agencies or large companies such as facebook.com, paypal.com, and the fake URLs may be faceboook.com, www.paypall.com. Leading the recipient to click on links or download data without hesitation. These virus emails infiltrate and infect your computer to steal personal/corporate information such as login passwords, bank accounts, etc.
Business Email Compromise, BEC
Business email compromise (BEC)—also known as email account compromise (EAC), is one of the most financially damaging online crimes. BEC fraud is carried out by impersonating the email accounts of high-level executives or public accounts. The content of the emails might be related to confidential or urgent tasks, and sent to company affiliates or financial institutions, suppliers, etc, guiding recipients through the process, such as intercepting legitimate company personal data, financial and other information, or even requesting remittances to fraudulent accounts.
The emails used in BEC scams are not sent on a large scale in order to avoid being marked as spam. In addition, BEC fraud will trick the victim into transferring money to the other party and usually requires the victim to do it quickly and privately. There was a case of BEC fraud in which the victim is the subsidiary of TOYOTA, causing the company’s nearly 4 billion yen financial loss!
How to avoid email fraud (email scam)?
1. Increase cyber security awareness
When you receive an email from someone for the first time, you need to take a moment to examine it carefully before you proceed. If there is an attachment with a link or file, request you provide personal information, or ask you to receive a free gift by clicking to the link, you should check whether the domain is correct carefully.
2. Install SSL Certificate – HTTPS
Nowadays, the SSL certificate is necessary for website security. The SSL certificate is used to ensure that the data transmitted between the user and the website is protected, including credit card number and personal information, ect. Customers will feel more relieved spending money on a SSL certified website.
Starting from January 2017, the Chrome browser will mark the websites that do not use https encryption but provide password transmission and credit cards service as “unsafe”, which will also be displayed on mobile devices. If you open the webpage and an “unsafe” warning is displayed, please do not enter your personal information, because reputable corporate and institutional websites will have SSL digital certificates installed, especially e-commerce websites!
3. Email Encryption
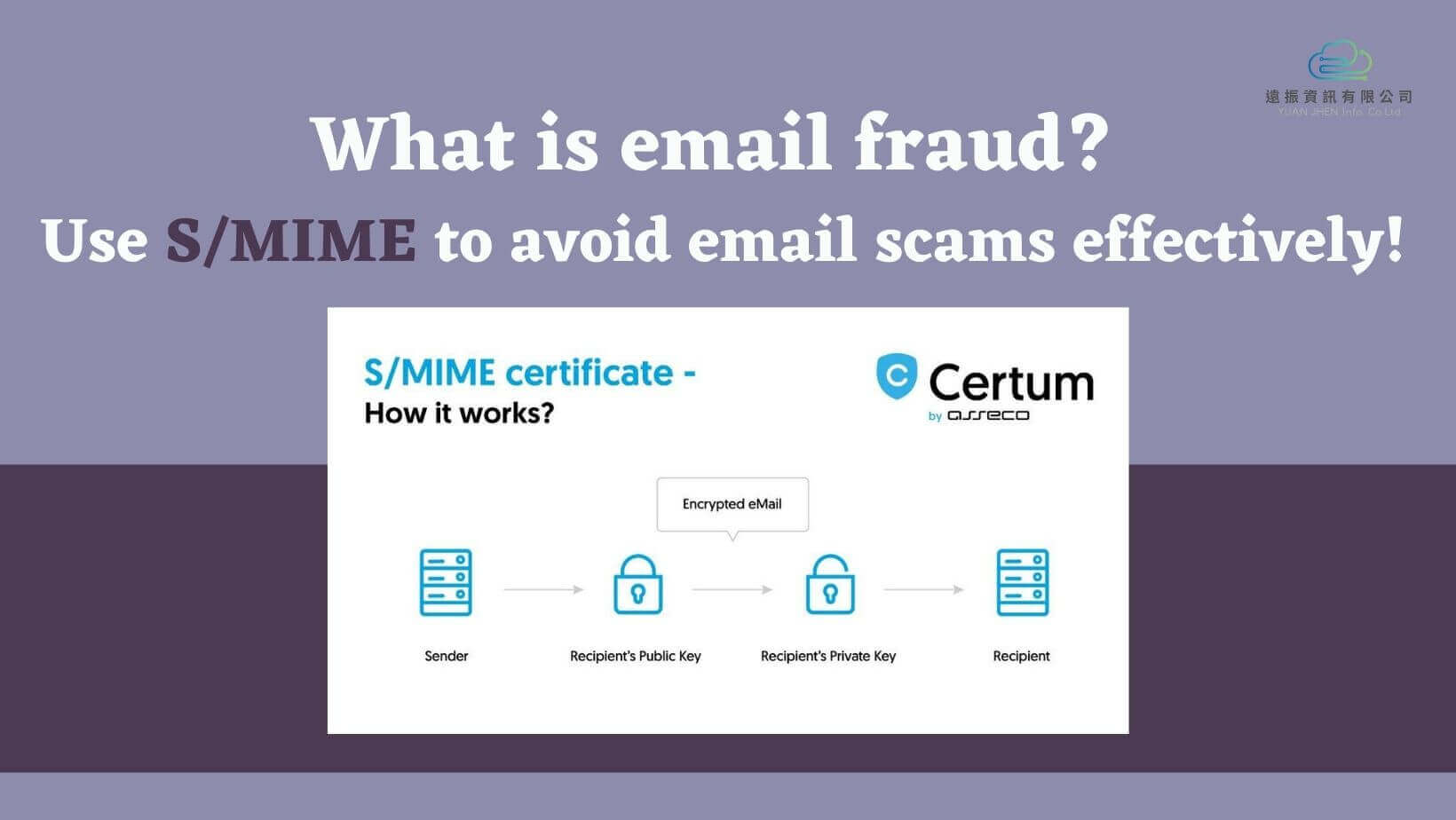
Email security is also one of the most important aspects of information security management. However, most emails do not have encryption and verification functions. Therefore, beside the encryption function with SSL certificate, there is also a certificate that provides an encryption function that is used for email – S/MIME certificates.
In order to prevent personal or corporate internal data from being stolen and tampered with when using email, companies should use email encryption and signature mechanisms to ensure email security. Therefore, S/MIME and other types of email encryption certificates are indispensable!
S/MIME – Email certificate recommendation
What is an S/MIME certificate?
S/MIME (Secure/Multipurpose Internet Mail Extensions), is an email encryption certificate which is a digital certificate using PKI technology for the signature and encryption of the email content. S/MIME is the highest certificate level (Class 3) of Certum Email ID. It can encrypt email communication and provide digital signatures to verify the authenticity of the sender and effectively resist common email scams such as phishing, BEC.
*Class 3: In addition to the verification of personal name, company registered name or website URL and general related information when registering for Class 3 Certificate, users must provide legal and correct certification documents, and they must apply in person and provide sufficient certification documents to identify the applicant. This level of verification is also called extended verification (EV).
▶ Know more about S/MIME ➜ S/MIME – Email ID Certificate
S/MIME features
1. Email Encryption
S/MIME is an email encryption format developed by using public key infrastructure (PKI) to encrypt multimedia messages (MIME). When encrypted email is transmitted, confidentiality and integrity can be ensured. Only the intended recipient can read encrypted emails, unauthorized persons cannot read encrypted emails, nor can they intercept and modify email content during transmission. Mail encryption provides two specific security services:
-
Email confidentiality:
Before sending an email, you can pre-set the recipient as the only person who can receive or view the content of the email. Emails will provide confidentiality during transmission and storage. -
Data integrity:
If used with email digital signatures, email encryption feature can help you to protect data integrity, because certain encryption operations may occur.
2. Email Signature
Email signature, also known as email digital signature (Digital Signature), is used to identify and confirm the identity, information, and authenticity of the email signer, so that the recipient can verify whether the email is authentic. Email signature can eliminate the risk of BEC fraud.
S/MIME helps you verify the client for commercial purposes which is suitable for trading confidential, government data, medical records, financial electronics or digital communications. The digital signature provides the following security features:
-
Email verification:
Digital Signature is used to verify identity, providing identification of the entity and other owners. Basically, an SMTP email cannot know the sender, but a digital signature can verify the authenticity of your identity to the recipient. -
Email non-repudiation:
Digital Signature will compulsorily recognize signature provided, legal information, and the verified signature cannot be denied. -
Data integrity:
When the recipient of a digitally signed email verifies the digital signature, the recipient can assure the received email. Once the email has been signed, any changes made during transmission will be invalid to ensure the data integrity of the mail.

▼ S/MIME encryption principle

▶ Know more about S/MIME ➜ S/MIME – Email ID Certificate